Like other AWS services, AWS CloudFormation is integrated with AWS CloudTrail for logging its API activities. It’s interesting to note how a single CLI command from your Terminal translates into multiple API calls in the background, all targeted toward realizing the infrastructure stack described in your CloudFormation template.
AWS CloudTrail’s event history describes all the event payloads from the APIs triggered by the service on your behalf. Let’s see what events are logged during the creation of a simple stack:
Let’s deploy our stack in the eu-central-1 region using the AWS CLI:
aws cloudformation deploy \
–stack-name devops-simplified-test \
–template-body file://template.yml \
–region eu-central-1
Once the stack has been created, you can see the logged API calls in the CloudTrail console. These are highlighted in Figure 4.2:
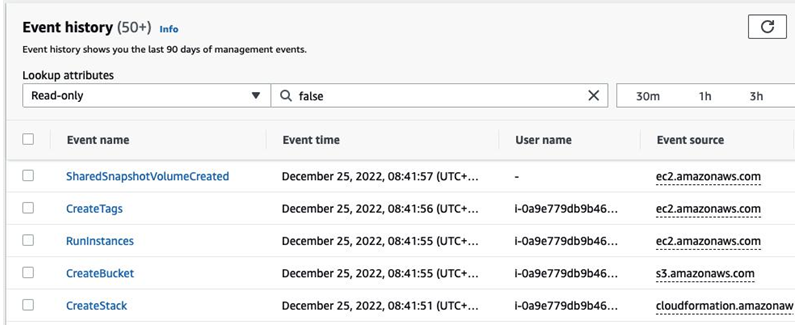
Figure 4.2: API calls logged in CloudTrail as a result of stack creation
How CloudFormation works 67
The following sequence of events was logged in CloudTrail:
- Stack creation triggered by the user resulted in the CreateStack event being logged.
- CloudFormation invoked the respective APIs from the EC2 and S3 services to create the resources defined in the template. These events were logged as CreateBucket and RunInstances.
- CloudFormation requested the assignment of relevant tags on the EC2 instance. These tags identify the stack-name and stack-id properties that created the instance. The event type in this case was CreateTags.
- Finally, we can see the SharedSnapshotVolumeCreated event log, which was a result of the EC2 service requesting a volume creation from an existing snapshot.
These audit logs are very important to understand the service behavior and dissect the activities happening behind the scenes. Typically, organizations set up forwarding of CloudTrail trails to a centralized S3 bucket for audit purposes. This data is sometimes also forwarded toSecurity Information and Event Management (SIEM) systems.